Why browser isolation is still hard
Modern browsers have become the primary interface to sensitive systems — cloud consoles, financial dashboards, internal admin tools, customer data platforms, and third-party SaaS applications.
Despite this, browsers remain fundamentally stateful:
- Cookies persist across sessions
- Local storage and IndexedDB accumulate data
- Browser fingerprints remain stable
- Cached credentials and artifacts survive far longer than intended
Common mitigations such as incognito mode, VPNs, or endpoint hardening solve only parts of the problem. They do not address session-level contamination, especially when the same machine is used for:
- Client demos
- Administrative access
- Research on untrusted sites
- Work from public or semi-trusted networks
The core issue is simple:
Browsers were never designed to be disposable.
This article explores a practical architecture for ephemeral browser sessions, where each browsing session is isolated, short-lived, and destroyed by design.
What are we actually protecting against?
Before discussing architecture, it’s important to define a realistic threat model.
In-Scope threats
- Cross-session data leakage
Cookies, tokens, or cached credentials leaking between workflows - Browser fingerprint persistence
Trackers correlating activity across sessions - Residual artifacts
Files, cache entries, clipboard data, and local storage remnants - Compromised websites
Malicious scripts persisting state beyond intended scope - Shared or semi-trusted endpoints
Public Wi-Fi, shared laptops, contractor machines
Out-of-Scope (for this design)
- Kernel-level host compromise
- Hardware-based attacks
- Malicious insiders with host access
The goal is risk reduction through isolation, not absolute security.
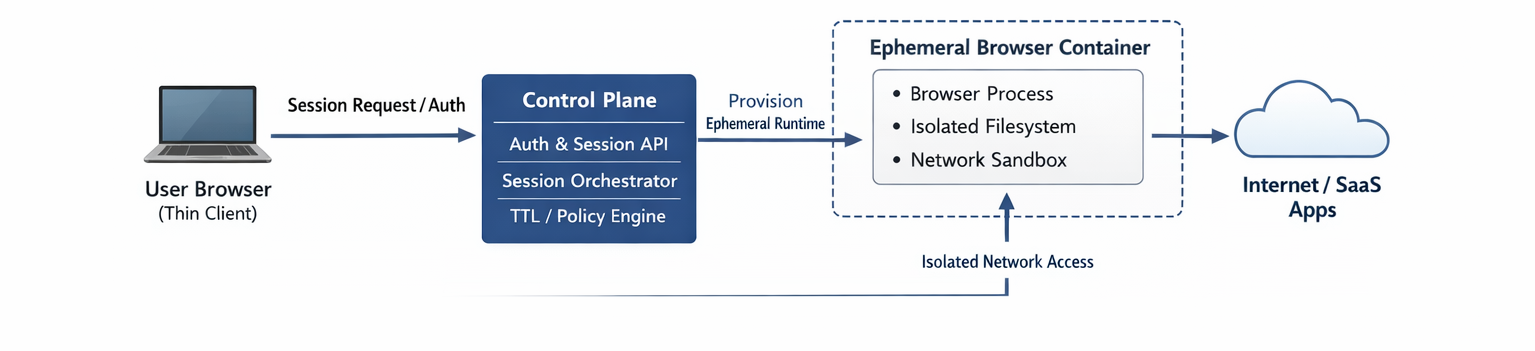
Architectural overview: Disposable by design
At a high level, the system treats each browser session as a short-lived compute workload, not as an application running on a long-lived device.
Core principle
One session = one isolated runtime = zero persistence
High-level flow
- User requests a new browser session
- Backend provisions an isolated container
- Browser runs inside the container
- User interacts via a remote stream
- Session expires or is terminated
- Container and all state are destroyed
High-level architecture
Isolation mechanisms: How containment is enforced
Process & namespace isolation
Each browser session runs inside its own container with:
- PID namespace isolation
- User namespace isolation
- Dedicated filesystem mount
This ensures:
- No visibility into other sessions
- No shared process state
Filesystem isolation
- Read-only base image
- Ephemeral writable layer
- No persistent volumes
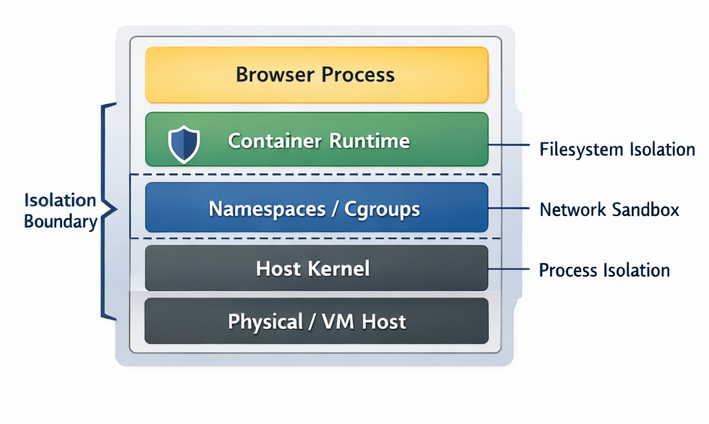
Network sandboxing
Each container receives:
- Isolated network namespace
- Controlled outbound access
- Optional egress filtering
This prevents:
- Lateral movement
- Session-to-session network correlation
Resource constraints
Containers enforce:
- CPU limits
- Memory caps
- Hard session TTL
This guarantees:
- Predictable cost
- Forced termination of stale sessions
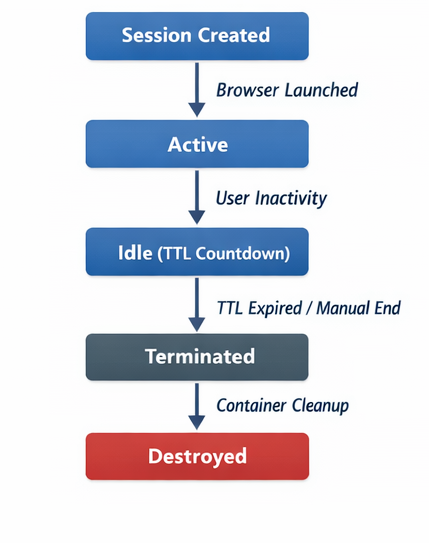
Session lifecycle management
Ephemerality must be enforced at the platform level, not left to user behavior.
Lifecycle states
- Provisioning
- Active
- Idle (TTL countdown)
- Termination
- Destruction
Design trade-offs and decisions
Cold start latency
- Container startup adds delay
- Mitigations:
- Warm pools
- Lightweight images
- Optimized browser builds
Performance vs isolation
- Full isolation costs more than shared processes
- Chosen deliberately for:
- Predictability
- Security clarity
- Easier reasoning about risk
UX vs Security
- No “resume session”
- No saved state
- Intentional friction to prevent unsafe reuse
These are conscious decisions, not limitations.
Practical applications
This approach is especially useful for:
- Accessing financial or admin dashboards
- Client demonstrations
- Researching untrusted content
- Working from public or semi-trusted networks
- Contractors handling sensitive systems
In all cases, the goal is to limit blast radius.
Conclusion
As browser usage increasingly overlaps with sensitive workflows, traditional endpoint-based security models show their limits.
Ephemeral, isolated browser sessions provide a practical middle ground:
- Strong isolation
- Clear lifecycle boundaries
- Predictable security properties
This architectural approach informed the design of a browser platform I am currently building, focused on privacy-first, disposable browsing for professional use cases.




