Introduction
Web browsers have evolved into powerful execution environments, routinely handling authentication tokens, privileged credentials, internal dashboards, and sensitive user data. Yet, most security controls still treat browsers as long-lived, trusted endpoints.
Disposable or ephemeral browser environments challenge this assumption by introducing session-scoped isolation and automatic destruction as first-class security controls.
This article presents a structured threat model for disposable browser environments, analyzing:
- Key threat categories
- Attack surfaces
- Mitigation strategies
- Residual risks and trade-offs
Security assumptions and scope
In scope
- Browser-level threats
- Session persistence risks
- Web-based attacks
- Untrusted networks and endpoints
- Data remanence across sessions
Out of scope
- Host kernel compromise
- Physical attacks
- Hardware-level exploits
- Insider threats with infrastructure access
The goal is risk containment, not absolute security.
Threat model overview
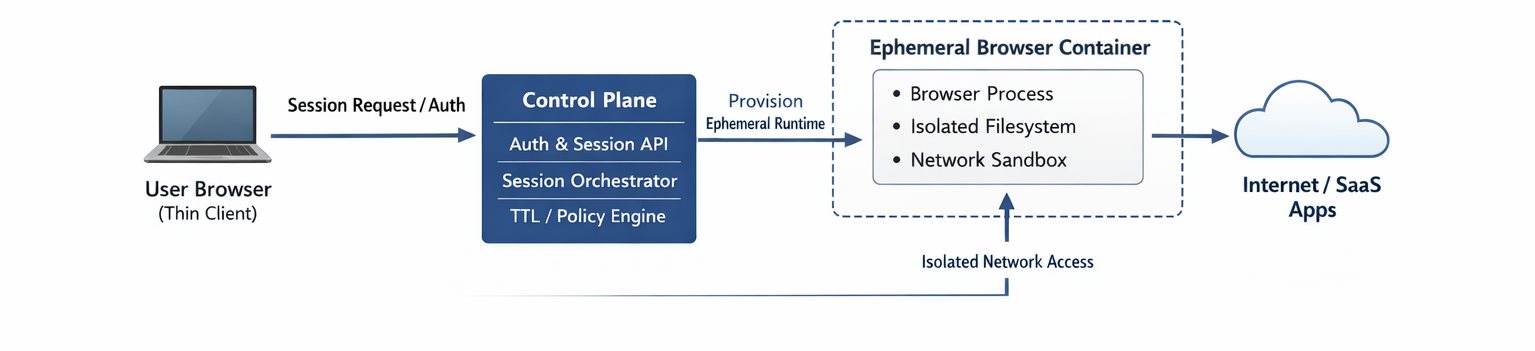
Disposable browser environments shift the security boundary from the endpoint to the session runtime.
Key Principle
A compromised session must never compromise another session.
Description:
- Users interact through a thin client
- Sessions are provisioned by a control plane
- Browsers run inside fully isolated, short-lived containers
- All state is destroyed at session termination
Threat categories
Persistent tracking & fingerprinting
Threat
- Cookies, IndexedDB, local storage
- Browser fingerprint correlation
- Cross-session tracking
Impact
- Identity correlation
- Behavioral profiling
- Privacy violations
Mitigation
- Per-session container runtime
- No shared filesystem
- Fresh browser instance per session
Credential & token leakage
Threat
- OAuth tokens cached in browser storage
- Saved credentials
- Session hijacking
Impact
- Unauthorized account access
- Privilege escalation
Mitigation
- No persistent storage
- Forced session TTL
- Container destruction guarantees cleanup
Malicious web content
Threat
- Drive-by malware
- Cryptomining scripts
- Persistent XSS payloads
Impact
- Long-term compromise
- Data exfiltration
Mitigation
- Process isolation
- Network sandboxing
- Non-persistent execution environment
Shared endpoint risk
Threat
- Public Wi-Fi
- Shared workstations
- Contractor devices
Impact
- Session reuse
- Local data leakage
Mitigation
- Browser runs remotely
- Endpoint receives only rendered output
- No sensitive data stored locally
Attack surface analysis
Reduced Surfaces
- Local disk persistence
- Cross-session contamination
- Credential reuse
Remaining Surfaces
- Browser engine vulnerabilities
- Control plane misconfiguration
- Session streaming layer
Disposable environments reduce blast radius, not eliminate all risk.
Control plane threats
The control plane becomes a high-value asset.
Threats
- Unauthorized session creation
- TTL bypass
- Policy misconfiguration
Controls
- Strong authentication
- Session lifecycle enforcement
- Audit logging
- Rate limiting
Security shifts from endpoint sprawl to centralized enforcement.
Trade-offs and residual risks
Performance
- Cold start latency
- Resource overhead
UX
- No session resume
- No personalization persistence
Cost
- Compute per session
These are intentional trade-offs made to achieve deterministic security behavior.
Conclusion
Disposable browser environments introduce a fundamentally different security model — one that assumes compromise is possible and designs for containment and automatic recovery.
By enforcing:
- Isolation by default
- Short-lived execution
- Mandatory destruction
This architecture significantly reduces the risk of data leakage, session hijacking, and long-term compromise.
The threat model outlined here informed the design of a browser platform I am currently building, focused on privacy-first, ephemeral browsing for professional use cases.




